Fertiger #Luxshare: #Ransomware-Gruppe will #Apple  -Daten erbeutet haben | Mac & i https://www.heise.de/news/Fertiger-Luxshare-Ransomware-Gruppe-will-Apple-Daten-erbeutet-haben-11151231.html #Malware
-Daten erbeutet haben | Mac & i https://www.heise.de/news/Fertiger-Luxshare-Ransomware-Gruppe-will-Apple-Daten-erbeutet-haben-11151231.html #Malware
Fertiger #Luxshare: #Ransomware-Gruppe will #Apple  -Daten erbeutet haben | Mac & i https://www.heise.de/news/Fertiger-Luxshare-Ransomware-Gruppe-will-Apple-Daten-erbeutet-haben-11151231.html #Malware
-Daten erbeutet haben | Mac & i https://www.heise.de/news/Fertiger-Luxshare-Ransomware-Gruppe-will-Apple-Daten-erbeutet-haben-11151231.html #Malware
149 Million Usernames and Passwords Exposed by Unsecured Database
This “dream wish list for criminals” includes millions of Gmail, Facebook, banking logins, and more. The researcher who discovered it suspects they were collected using infostealing malware.
149 Million Usernames and Passwords Exposed by Unsecured Database
This “dream wish list for criminals” includes millions of Gmail, Facebook, banking logins, and more. The researcher who discovered it suspects they were collected using infostealing malware.
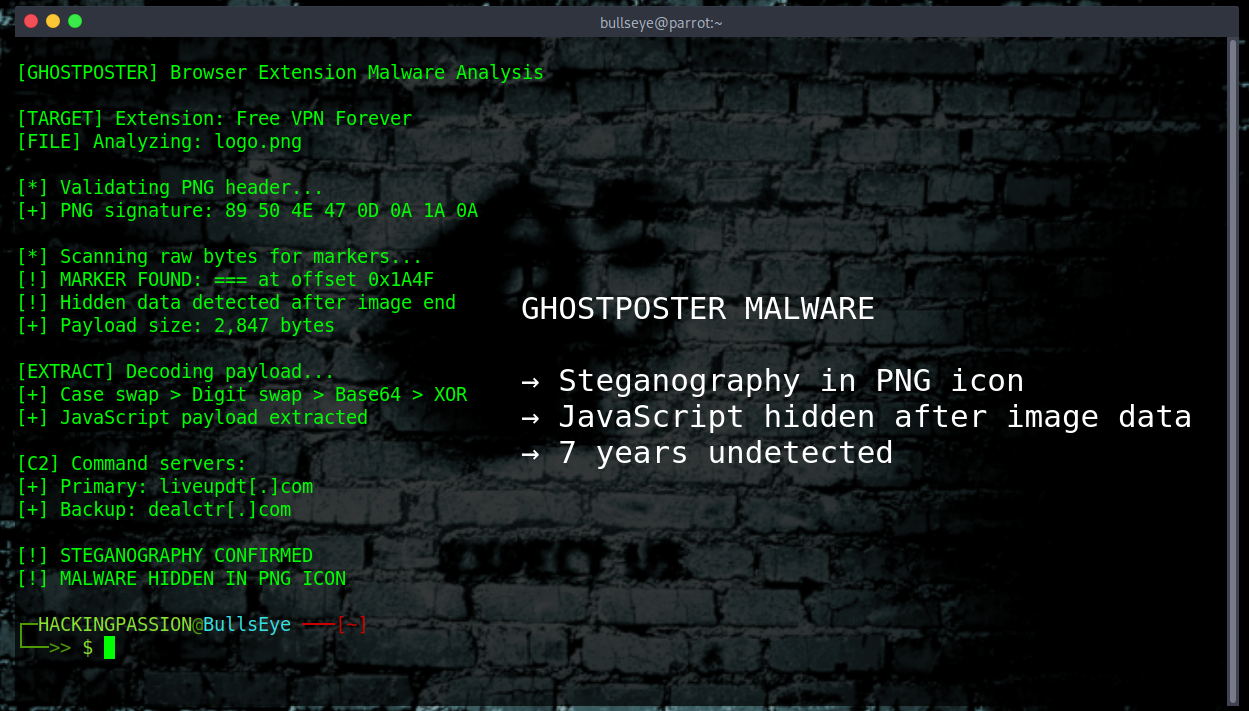
Check your #browser extensions, some are hiding JavaScript #malware in PNG images https://hackingpassion.com/ghostposter-malware-browser-extension-png-steganography/
Check your #browser extensions, some are hiding JavaScript #malware in PNG images https://hackingpassion.com/ghostposter-malware-browser-extension-png-steganography/
Inside MacSync's Script-Driven Stealer and Hardware Wallet App Trojanization
MacSync is a sophisticated macOS infostealer that targets cryptocurrency users. It is delivered through a phishing lure disguised as a cloud storage installer, tricking users into executing a malicious Terminal command. The malware employs a multi-stage infection process, using a script-based approach to harvest browser credentials, cryptocurrency wallet data, and sensitive files. A key feature of MacSync is its ability to trojanize popular Electron-based cryptocurrency applications like Ledger and Trezor, enabling long-term phishing and data exfiltration. The malware's infrastructure includes multiple rotating C2 domains and clone sites, indicating an ongoing and evolving campaign. MacSync's focus on cryptocurrency-related data and its stealthy, script-based execution make it particularly dangerous for macOS users in the crypto community.
Pulse ID: 69711eea5249f136051acf6c
Pulse Link: https://otx.alienvault.com/pulse/69711eea5249f136051acf6c
Pulse Author: AlienVault
Created: 2026-01-21 18:46:01
Be advised, this data is unverified and should be considered preliminary. Always do further verification.
#Browser #Cloud #CyberSecurity #Edge #InfoSec #InfoStealer #Mac #MacOS #Malware #OTX #OpenThreatExchange #Phishing #RAT #Trojan #bot #cryptocurrency #AlienVault
Inside MacSync's Script-Driven Stealer and Hardware Wallet App Trojanization
MacSync is a sophisticated macOS infostealer that targets cryptocurrency users. It is delivered through a phishing lure disguised as a cloud storage installer, tricking users into executing a malicious Terminal command. The malware employs a multi-stage infection process, using a script-based approach to harvest browser credentials, cryptocurrency wallet data, and sensitive files. A key feature of MacSync is its ability to trojanize popular Electron-based cryptocurrency applications like Ledger and Trezor, enabling long-term phishing and data exfiltration. The malware's infrastructure includes multiple rotating C2 domains and clone sites, indicating an ongoing and evolving campaign. MacSync's focus on cryptocurrency-related data and its stealthy, script-based execution make it particularly dangerous for macOS users in the crypto community.
Pulse ID: 69711eea5249f136051acf6c
Pulse Link: https://otx.alienvault.com/pulse/69711eea5249f136051acf6c
Pulse Author: AlienVault
Created: 2026-01-21 18:46:01
Be advised, this data is unverified and should be considered preliminary. Always do further verification.
#Browser #Cloud #CyberSecurity #Edge #InfoSec #InfoStealer #Mac #MacOS #Malware #OTX #OpenThreatExchange #Phishing #RAT #Trojan #bot #cryptocurrency #AlienVault
And now for something completely different: If you’re using a Mac and are interested in opening files of dubious origin and content, this article might be interesting for you.
https://eclecticlight.co/2026/01/12/how-to-open-a-suspicious-document-or-app/
#cybersecurity #dataprotection #malware #macos #appple #dangerzone #viables
And now for something completely different: If you’re using a Mac and are interested in opening files of dubious origin and content, this article might be interesting for you.
https://eclecticlight.co/2026/01/12/how-to-open-a-suspicious-document-or-app/
#cybersecurity #dataprotection #malware #macos #appple #dangerzone #viables
And now for something completely different: If you’re using a Mac and are interested in opening files of dubious origin and content, this article might be interesting for you.
eclecticlight.co/2026/01/12/h...
#cybersecurity #dataprotection #malware #macos #appple #dangerzone #viables
How to open a suspicious docum...
And now for something completely different: If you’re using a Mac and are interested in opening files of dubious origin and content, this article might be interesting for you.
eclecticlight.co/2026/01/12/h...
#cybersecurity #dataprotection #malware #macos #appple #dangerzone #viables
How to open a suspicious docum...
New, from me: The Kimwolf Botnet is Lurking in Corporate, Govt. Networks
A new Internet-of-Things botnet called Kimwolf has spread to more than 2 million devices, forcing infected systems to participate in massive distributed denial-of-service (DDoS) attacks and to relay other malicious and abusive Internet traffic. Kimwolf’s ability to scan the local networks of compromised systems for other IoT devices to infect makes it a sobering threat to organizations, and new research reveals Kimwolf is surprisingly prevalent in government and corporate networks.
https://krebsonsecurity.com/2026/01/kimwolf-botnet-lurking-in-corporate-govt-networks/